Increase Cybersecurity and Protect Your Assets
More Data, More Money, More Cybercrime
For several years, we have witnessed the data revolution. The internet, data, and technology are inextricably linked. In an era of unprecedented data proliferation, the increase in daily internet usage results in greater volumes of data being used, produced, and stored. This volume of information generated each day continues to grow and is showing no signs of slowing down.
The exponential increase in data also introduces more threats. The phrase “data is the new oil” reflects the immense value of data as a contemporary asset. Just as there have been global conflicts over precious resources, data is now a critical battleground, albeit in the digital domain rather than on traditional battlefields.

As the digital economy expands, cybercrime is escalating in parallel. The surge in online and mobile interactions creates billions of potential vulnerabilities. These often lead to data breaches, posing substantial risks to both individuals and businesses. It is crucial for enterprises and individuals to proactively protect their sensitive information from the increasing threat of exposure and to develop robust strategies to mitigate the impacts of a breaches.
When businesses fall victim to cyberattacks, they face substantial costs stemming from operational disruptions and adjustments to business practices. Companies must reassess their data collection and storage practices to safeguard sensitive information more effectively. Companies that experience breaches compromising their customers’ data frequently shell out millions to settle claims. These claims are not driven only by civil lawsuits – regulators have long realized the importance of enterprises protecting customer and user data.
For example, Europe’s General Data Protection Regulations (GDPR) was the first data privacy law passed (April 2016) and is intense. GDPR imposes obligations to all organizations, regardless of where they are domiciled, if they have consumers in the EU. Under GDPR, companies must:
- only process personal data unless one of 6 conditions are met
- ensure data is secure for consumers
- disclose data breaches to consumers within 72 hours
- demonstrate their personal data practices are compliant with regulations

Many countries, states, and provinces have used GDPR as the modern blueprint for revisions to their data policies.
California was first in the United States to introduce significant data privacy laws with the introduction of the California Consumer Privacy Act (CCPA). Whereas GDPR focuses on making privacy a legal framework, CCPA focuses on personal data transparency. Under CCPA, consumers have the right to:
- know what personal data is collected
- have companies delete any personal data collected
- opt out of third-party selling of personal data
- non-discrimination (businesses cannot deny goods or services, charge a different price, or provide an extra level or quality of goods and services) for exercising their CCPA rights.
However, the impact of cybercrime extends beyond financial ramifications. The most significant losses often arise from reputational harm. Customers are increasingly concerned about how businesses manage security issues and are inclined to support businesses that are transparent and vocal about the security measures they have implemented.
Growing Problems
Nobody is safe from cybercrime. Cyberattacks target entities of all sizes and sectors, including individuals, corporations, and governments. We frequently access financial information online, shop online, share personal details on social media, and handle sensitive business and government documents remotely. With our increasing reliance on digital platforms, we become more vulnerable to various cybersecurity risks. Malicious hackers exploit security weaknesses to capitalize on individuals’ personal data and the expanding digital footprints of organizations.
The Federal Bureau of Investigation’s (FBI) Internet Crime Complaint Center reported that the American public totalled ~900,000 complaints with potential losses of US$12.5 billion from cybercrime in 2023. This uptick represents a 22% increase in losses compared to 2022 (Exhibit 1).
Exhibit 1: Complaints and Losses Over the Last Five Years from Cybercrime
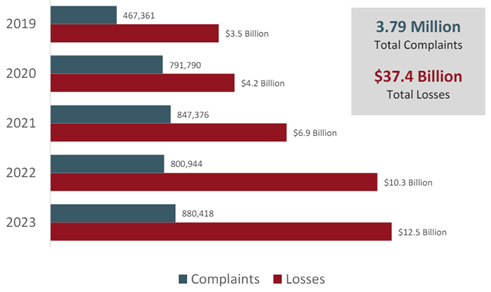
Given the escalating threats of financial fraud, unauthorized access, and identity theft, the importance of robust cybersecurity measures has never been more critical. Cybercriminals cast a wide net when searching for targets. Most people are familiar with scam attempts via SMS, social media, email, and phone calls, however entire business and service sectors face cybercrime on a significantly larger scale.
Data Breaches
Due to the interconnected nature of digital systems and the vast amount of personal information stored online, cybercrime frequently serves as a gateway to identity theft. Hackers employ tactics such as phishing emails, malware, and data breaches to gain unauthorized access to sensitive data. Between 2021-2023, data breaches surged by 72%, with 94% of organizations reporting email security incidents.
An IBM report showed that in 2023, the global average cost of a data breach was US$4.45 million, a 15% rise over the preceding three years. Consequently, 51% of organizations intend to boost security investments in response to breaches, focusing on areas such as incident response planning and testing, employee training, and the deployment of threat detection and response tools. Notably, organizations extensively leveraging security artificial intelligence and automation achieve an average savings of US$1.76 million compared to their counterparts that do not employ such technologies.

In a specific case, the personal data of 73 million current and former AT&T customers was leaked online in March 2024. According to the US telecom giant, information such as addresses, social security numbers, and passcodes were published on the dark web, although AT&T stated that financial information was not part of the breach. A class action lawsuit was filed March 30 in the US District Court for the Northern District of Texas against AT&T stating that the company recklessly maintained customers personally identifiable information and failed to properly safeguard its system. The lawsuit has not been settled yet. For comparison, in 2022 T-Mobile agreed to pay US$350 million to settle a class-action lawsuit after personal data of more than 50 million customers was leaked and agreed to spend an additional $US$150 million to upgrade data security.
Streaming service ROKU identified nearly 600,000 compromised accounts in two distinct cyberattacks in April 2024. Approximately 400 hacked accounts were utilized by hackers to subscribe to unauthorized services. The company has pledged to refund or reverse charges for accounts affected by unauthorized purchases resulting from the attack.
In May 2024, Ticketmaster experienced a significant hack affecting over half a billion users. The breach allegedly exposed emails, phone numbers, addresses, and even financial details. A notorious hacker group is reportedly selling the 1.3 terabyte-sized trove of data for a one-time price of US$500,000 on a popular hacking forum.
Also in May 2024, malware stole credentials from 361 million Telegram accounts. This represented about 122GB of credentials that included email addresses and passwords.
Ransomware
Ransomware also represents a prevalent form of cyber-extortion, using malicious software to seize control of a user’s computer system and withhold access until a ransom is paid.According to Chainalysis, in 2023 cybercriminals extorted US$1.1 billion in ransom payments, up from US$567 million in 2022.

The Chainalysis report does not account for additional losses, often totaling millions of dollars, incurred by victims as they strive to recover from ransomware attacks. MGM Resorts, for example, estimated its recovery costs from a significant ransomware incident in October 2023 was US$100 million.
The ransomware attack that compelled major U.S. fuel operator Colonial Pipeline to halt operations in May 2021 elevated ransomware to a top national security concern for the Biden Administration. In response, the U.S. Treasury has sought to curb ransom payments through sanctions. However, cybercriminals are adapting to these measures, and the issue remains pervasive, particularly affecting U.S. schools and local governments lacking the resources to adequately defend themselves.
In December 2022, the Hospital for Sick Children (SickKids) in Toronto announced a ‘code grey’, which meant that it had experienced one or more system failures. This turned out to be another ransomware attack. This attack was unique because the provider of the ransomware-as-a-service infrastructure, the LockBit Group, publicly apologized for the incident. The group blamed one of its “partners,” a euphemism for a customer using its ransomware-as-a-service offering, for the attack. LockBit provided unlock codes to decrypt the scrambled data.
Pay Now, Save Later
Investing in cybersecurity is more effective when done sooner rather than later. Companies looking to safeguard themselves from online threats often face significant financial investments. These expenditures may include:
- Cybersecurity technology and expertise acquisition;
- Expenses associated with notifying affected parties in the event of a breach;
- Payment of insurance premiums for cybersecurity coverage;
- Engagement of public relations support to manage reputational fallout;
- Hiring of legal and other experts to ensure compliance with cybersecurity regulations, and;
- Potential additional costs for attorney fees and damages resulting from civil cases against the company in the aftermath of an attack.
Equifax, one of the leading credit bureaus, learned this lesson the hard way following a 2017 data breach that compromised the personal data of 147 million customers. As a consequence of ensuing litigation, the company agreed to pay up to US$425 million to help consumers recover.
In July 2022, T-Mobile disclosed the terms of a settlement for a consolidated class action lawsuit resulting from a data breach in early 2021, impacting approximately 77 million individuals. The breach involved “unauthorized access” to T-Mobile’s systems with a portion of customer data listed for sale on a known cybercriminal forum. According to an SEC filing, T-Mobile agreed to pay a total of $350 million to cover claims submitted by class members, the legal fees of plaintiffs’ counsel, and the administrative costs of the settlement. Additionally, the company committed to an aggregate incremental expenditure of $150 million for data security and related technology in 2022 and 2023.
Long-term costs from breaches, particularly in fines and settlements, can be significant. In 2014, Home Depot experienced a significant data breach. Attackers gained access to the network using stolen credentials, compromising the point-of-sale system, and pilfering over 50 million credit card numbers and 53 million email addresses between April and September 2014. The breach cost Home Depot at least US$134.5 million in payouts to credit card companies and banks. Then in 2016, the company settled for US$19.5 million to compensate affected customers and cover credit monitoring expenses. Additionally, in 2017, Home Depot agreed to a US$25 million settlement with financial institutions affected by the breach. Furthermore, in November 2020, Home Depot settled for US$17.5 million with 46 U.S. states and Washington D.C. The settlement requires Home Depot to appoint a highly qualified Chief Information Security Officer, provide security training for key personnel, and implement robust security controls and policies.
Cybersecurity is a Fiduciary Duty
While challenging to precisely measure, companies affected by major cyberattacks may also experience considerable damage to their brand equity. Both customers and even suppliers may feel less safe entrusting their sensitive data to a company that has experienced IT infrastructure breaches in the past.
In addition to diminished institutional trust, research indicates that publicly traded companies are prone to experiencing a short-term decrease in market value. The IBM Security Cost of a Data Breach Report revealed that nearly all organizations examined witnessed a downturn in quarterly earnings and stock prices following a data breach.
A study by Morningstar Sustainalytics looked at how the stock prices of 69 major companies reacted to cyberattacks. They compared the price changes of these companies over 120 days after the attack to the overall market trend (S&P 500). The study found that the stock prices of the companies dropped by an average of 2.3% within four days of the incident. This decline continued, reaching a low point of 4.6% around two months later. Even a year after the cyberattacks, the stocks in the incident portfolio still underperformed the market, with an average return of -0.65%. This is a significant drop compared to the 8.47% average return these same stocks had in the year before the attacks. This suggests that major cyberattacks can have a lasting negative impact on a company’s stock price.
These financial setbacks are compounded by reported costs exceeding US$1 billion, encompassing regulatory fines, legal expenses, and settlements with consumers, businesses, and states.
Intangible assets represent approximately 90% of the value of S&P 500 companies. A company’s product designs, technologies, and market strategies constitute are valuable assets, however, much of this intellectual property (IP) is stored in the cloud, making it susceptible to cyberattacks. The total cost from theft of American IP was estimated to be US$1.12 billion in 2023, a 36% increase from US$822.3 million in 2022.
Conclusion
We are in the midst of a data revolution. As the digital economy grows, cybercrime is simultaneously increasing. Businesses hit by cyberattacks incur significant costs with the impact of extending beyond financial losses. Cybersecurity is meant to protect devices, networks, and data from unauthorized access and criminal use, but no one is immune to cybercrime. Entities of all sizes and sectors, including individuals, corporations, and governments are susceptible, which is why they must invest to protect their sensitive information and their brand.
Coming Up
In our next report we will discuss the potential market opportunity for Cybersecurity and highlight tailwinds in the sector.
For More Research
Access more Plurilock Security research HERE
Sign up for Sophic Capital’s reports HERE
Disclosures
Plurilock Security Inc. [TSXV:PLUR, OTC:PLCKF] has contracted Sophic Capital for capital markets advisory and investor relations services.
Disclaimers
The information and recommendations made available through our emails, newsletters, website and press releases (collectively referred to as the “Material”) by Sophic Capital Inc. (“Sophic” or “Company”) is for informational purposes only and shall not be used or construed as an offer to sell or be used as a solicitation of an offer to buy any services or securities. In accessing or consuming the Materials, you hereby acknowledge that any reliance upon any Materials shall be at your sole risk. None of the information provided in our monthly newsletter and emails or any other Material should be viewed as an invite, and/or induce or encourage any person to make any kind of investment decision. The recommendations and information provided in our Material are not tailored to the needs of particular persons and may not be appropriate for you depending on your financial position or investment goals or needs. You should apply your own judgment in making any use of the information provided in the Company’s Material, especially as the basis for any investment decisions. Securities or other investments referred to in the Materials may not be suitable for you and you should not make any kind of investment decision in relation to them without first obtaining independent investment advice from a qualified and registered investment advisor. You further agree that neither Sophic, its, directors, officers, shareholders, employees, affiliates consultants, and/or clients will be liable for any losses or liabilities that may be occasioned as a result of the information provided in any of the Material. By accessing Sophic’s website and signing up to receive the Company’s monthly newsletter or any other Material, you accept and agree to be bound by and comply with the terms and conditions set out herein. If you do not accept and agree to the terms, you should not use the Company’s website or accept the terms and conditions associated to the newsletter signup. Sophic is not registered as an adviser or dealer under the securities legislation of any jurisdiction of Canada or elsewhere and provides Material on behalf of its clients pursuant to an exemption from the registration requirements that is available in respect of generic advice. In no event will Sophic be responsible or liable to you or any other party for any damages of any kind arising out of or relating to the use of, misuse of and/or inability to use the Company’s website or Material. The information is directed only at persons resident in Canada. The Company’s Material or the information provided in the Material shall not in any form constitute as an offer or solicitation to anyone in the United States of America or any jurisdiction where such offer or solicitation is not authorized or to any person to whom it is unlawful to make such a solicitation. If you choose to access Sophic’s website and/or have signed up to receive the Company’s monthly newsletter or any other Material, you acknowledge that the information in the Material is intended for use by persons resident in Canada only. Sophic is not an investment advisor, nor does it maintain any registrations as such, and Material provided by Sophic shall not be used to make investment decisions. Information provided in the Company’s Material is often opinionated and should be considered for information purposes only. No stock exchange or securities regulatory authority anywhere has approved or disapproved of the information contained herein. There is no express or implied solicitation to buy or sell securities. Sophic and/or its principals and employees may have positions in the stocks mentioned in the Company’s Material and may trade in the stocks mentioned in the Material. Do not consider buying or selling any stock without conducting your own due diligence and/or without obtaining independent investment advice from a qualified and registered investment advisor. The Company has not independently verified any of the data from third party sources referred to in the Material, including information provided by Sophic clients that are the subject of the report, or ascertained the underlying assumptions relied upon by such sources. The Company does not assume any responsibility for the accuracy or completeness of this information or for any failure by any such other persons to disclose events which may have occurred or may affect the significance or accuracy of any such information.
The Material may contain forward looking information. Forward-looking statements are frequently, but not always, identified by words such as “expects,” “anticipates,” “believes,” “intends,” “estimates,” “potential,” “possible,” “projects,” “plans,” and similar expressions, or statements that events, conditions or results “will,” “may,” “could,” or “should” occur or be achieved or their negatives or other comparable words and include, without limitation, statements regarding, projected revenue, income or earnings or other results of operations, strategy, plans, objectives, goals and targets, plans to increase market share or with respect to anticipated performance compared to competitors, product development and adoption by potential customers. These statements relate to future events and future performance. Forward-looking statements are based on opinions and assumptions as of the date made and are subject to a variety of risks and other factors that could cause actual events/results to differ materially from these forward-looking statements. There can be no assurance that such expectations will prove to be correct; these statements are no guarantee of future performance and involve known and unknown risks, uncertainties and other factors. Sophic provides no assurance as to future results, performance, or achievements and no representations are made that actual results achieved will be as indicated in the forward-looking information. Nothing herein can be assumed or predicted, and you are strongly encouraged to learn more and seek independent advice before relying on any information presented.


